This post is the first in a series of posts that focus on the global proliferation and use of Hacking Team’s RCS spyware, sold exclusively to governments.
Summary
- Ethiopian Satellite Television Service1 (ESAT) is an independent satellite television, radio, and online news media outlet run by members of the Ethiopian diaspora. The service has operations in Alexandria, Virginia, as well as several other countries.2 ESAT’s broadcasts are frequently critical of the Ethiopian Government. Available in Ethiopia and around the world, ESAT has been subjected to jamming from within Ethiopia several times in the past few years.3 A recent documentary shown on Ethiopian state media warned opposition parties against participating in ESAT programming.4
- In the space of two hours on 20 December 2013, an attacker made three separate attempts to target two ESAT employees with sophisticated computer spyware, designed to steal files and passwords, and intercept Skype calls and instant messages. The spyware communicated with an IP address belonging to Ariave Satcom, a satellite provider that services Africa, Europe, and Asia.5 In each case, the spyware appeared to be Remote Control System (RCS), sold exclusively to governments by Milan-based Hacking Team.6
- Hacking Team states that they do not sell RCS to “repressive regimes”,7 and that RCS is not sold through “independent agents”.8 Hacking Team also says that all sales are reviewed by a board that includes outside engineers and lawyers. The board has veto power over any sale.9 Before authorizing a sale, the company states that it considers “credible government or non-government reports reflecting that a potential customer could use surveillance technologies to facilitate human rights abuses,” as well as “due process requirements” for surveillance.10
- The Committee to Protect Journalists (CPJ) reports that Ethiopia jails more journalists than any other African country besides Eritrea, and says that the Ethiopian government has shut down more than 75 media outlets since 1993.11 CPJ statistics also show that 79 journalists have been forced to flee Ethiopia due to threats and intimidation over the past decade, more than any other country in the world.12 A 2013 Human Rights Watch (HRW) report detailed ongoing torture at Ethiopia’s Maekelawi detention center, the first stop for arrested journalists and protests organizers. Former detainees described how they were: “repeatedly slapped, kicked, punched, and beaten,” and hung from the ceiling by their wrists. Information extracted in confession has been used to obtain conviction at trial, and to compel former detainees to work with the government.13 HRW also indicated abuses committed by the army, including the use of torture and rape to compel information from villagers near the site of an attack on a farm.14 HRW noted “insufficient respect for … due process” in Ethiopia.15
Background
Hacking Team and Remote Control System (RCS)
Hacking Team, also known as HT S.r.l., is a Milan-based purveyor of “offensive technology” to governments around the world. One of their products, known as Remote Control System (RCS), is a trojan that is sold exclusively to intelligence and law enforcement agencies worldwide. Hacking Team’s website describes the product as “the solution” to monitor targets that are increasingly using encryption, or those located outside the borders of the government that wants to monitor them.16
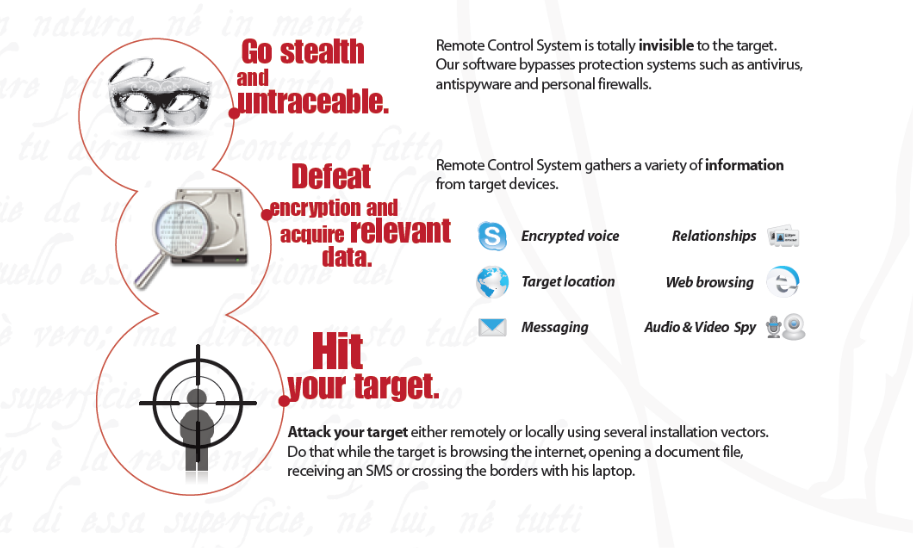 Description of RCS in a 2011 official brochure.17
Description of RCS in a 2011 official brochure.17
RCS infects a target’s computer or mobile phone to intercept data before it is encrypted for transmission, and can also intercept data that is never transmitted. For example, it can copy files from a computer’s hard disk, and can also record Skype calls, e-mails, instant messages, and passwords typed into a web browser.18 Furthermore, RCS can turn on a device’s webcam and microphone to spy on the user.19
While Hacking Team claims to potential clients that RCS can be used for mass surveillance of “hundreds of thousands of targets”,20 public statements by Hacking Team emphasize RCS’s potential use as a targeted tool for fighting crime and terrorism.21
Hacking Team was first thrust into the public spotlight in 2012 when RCS was used against award-winning Moroccan media outlet Mamfakinch,22 and United Arab Emirates (UAE) human rights activist Ahmed Mansoor, who was pardoned23 after serving seven months in prison for signing an online pro-democracy petition.24 Mansoor was infected, his GMail password was stolen, and his e-mails were downloaded.25 At the same time, RCS is apparently being used by foreign governments to target individuals on US soil.26,27
Evidence of the use of RCS against journalists and activists led Reporters Without Borders to name Hacking Team as one of the five “Corporate Enemies of the Internet”.28 Hacking Team Senior Counsel Eric Rabe responded with a defense of his company’s sales practices, in which he stated that Hacking Team does not provide its products to “repressive” regimes.29
On the issue of repressive regimes, Hacking Team goes to great lengths to assure that our software is not sold to governments that are blacklisted by the E.U., the U.S.A., NATO and similar international organizations or any “repressive” regime.
“Repressive” is a subjective term that may be difficult to define. We instead look to a selection of publications that rank countries based on freedom and democracy using a methodology. For example, The Economist publishes a Democracy Index,30 which rates governments around the world on a spectrum from “full democracies” to “authoritarian regimes.” Reporters Without Borders also publishes a yearly Press Freedom Index, which ranks countries’ press freedom situations from “good” to “very serious.”31
Ethiopia and Ethiopian Satellite Television Service (ESAT)
The Economist ranks Ethiopia as an “authoritarian regime,” and Reporters Without Borders classifies it as a country where there is a “difficult situation” for journalists. Human Rights Watch calls Ethiopia’s press law “deeply flawed,” and notes that several award-winning journalists have been convicted under the law for exercising their right to freedom of expression, as part of a government crackdown on independent media.32
Journalists jailed under the law include Eskinder Nega, who was convicted of terrorism in 2012 in a case following the publication of his column that criticized the government’s detention of journalists.33 Nega won the 2012 PEN America Freedom to Write Award, and was hailed by the group as of the “bravest and most admirable of writers, one who picked up his pen to write things that he knew would surely put him at grave risk”.34 Nega is currently serving an 18 year sentence in prison, having “[fallen] victim to exactly the measures he was highlighting”.35 In a May 2013 letter from prison, he wrote, “I will live to see the light at the end of the tunnel. It may or may not be a long wait. Whichever way events may go, I shall persevere!”36
ESAT describes itself as “powered by broad-based collective of exiled journalists, human rights advocates, civic society leaders and members in the Diaspora.” Available in Ethiopia around the world, ESAT’s television and radio signals have been subjected to jamming from within Ethiopia several times in the past few years.37
Previous research by the Citizen Lab found a version of the FinFisher government spyware that used a picture of members of Ethiopian opposition group Ginbot 7 as bait, indicating politically-motivated targeting. That spyware communicated with a command-and-control server in Ethiopia.38
First Targeting Attempt
First, the ESATSTUDIO Skype account was targeted with spyware. This account is used by ESAT for on-air interviews. The individual operating the ESATSTUDIO account at the time was an ESAT employee in Belgium, responsible for managing ESAT’s satellite broadcasts. An individual identified as “Yalfalkenu Meches” (Skype: yalfalkenu1) sent a file to ESATSTUDIO entitled “An Article for ESAT.rar.” We use Skype logs provided by the targets to illustrate the attacks.
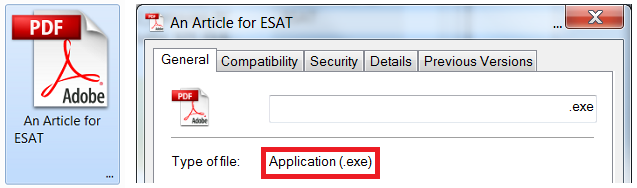
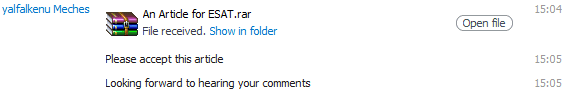 This .rar file contained an .exe file disguised as a .pdf. The file used the Adobe PDF icon, and contained a large number of spaces between the name and extension, to prevent Windows from displaying the extension.
This .rar file contained an .exe file disguised as a .pdf. The file used the Adobe PDF icon, and contained a large number of spaces between the name and extension, to prevent Windows from displaying the extension.
Despite the file’s name, “An Article for ESAT,” the file did not display any such article, or any other content, when opened.
Analysis and Link to Hacking Team RCS
Summary
The file sent to ESAT appeared to be Hacking Team’s RCS spyware for the following two reasons:
- The file communicated with a server that returned two SSL certificates. The second certificate was issued by “RCS Certification Authority” / “HT srl”, and was similar to SSL certificates returned by two other servers apparently owned by Hacking Team. The first certificate was similar to certificates returned by two other servers that appeared to be demonstration servers for Hacking Team’s RCS spyware.
- The file matched a signature that we had previously developed for RCS spyware.
Detailed Analysis
The hash of the file was:
Shortly after opening the .exe file, it attempted to communicate with the server 46.4.69.25 on port 80.
We probed the server and noticed that it returned two self-signed SSL certificates:39
| Issuer | Subject | Fingerprint |
| /CN=default | /CN=server | a7c0eacd845a7a433eca76f7d42fc3fedf1bde3c |
| /CN=RCS Certification Authority /O=HT srl | /CN=RCS Certification Authority /O=HT srl | 6500c243015a6ecc59f1272fec38eb0065d22063 |
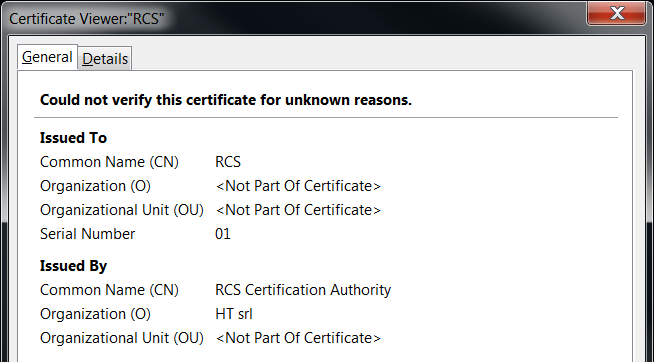 Hacking Team refers to their spyware as “RCS,” and identifies itself as “HT S.r.l.” on its website:
Hacking Team refers to their spyware as “RCS,” and identifies itself as “HT S.r.l.” on its website:
To confirm our hypothesis that these certificates were associated with Hacking Team, we searched historical SSL certificate data released by the Internet Census40 (443-TCP_SSLSessionReq) and by the University of Michigan’s zmap project.41 We found two servers returning the “RCS Certification Authority” / “HT srl” certificate that were in the following range:
The address and phone number on the range matches those on Hacking Team’s website. A Giancarlo Russo is listed as the COO of Hacking Team on LinkedIn.42 Thus, we believe that Hacking Team controls this range of IP addresses.
The two servers in this range that returned similar certificates to the server in the ESAT spyware were:
93.62.139.39 on 6/28/2012:
| Issuer | Subject | Fingerprint |
| /CN=RCS Certification Authority /O=HT srl | /CN=rcs-castore | deee895bf1f68e97cb997d929e0f991ecec6ab29 |
| /CN=RCS Certification Authority /O=HT srl | /CN=RCS Certification Authority /O=HT srl | 1e8e8806aa605544cda2bbb906b5d0cc7fb6fff7 |
93.62.139.42 on 8/12/2012:
| Issuer | Subject | Fingerprint |
| /CN=RCS Certification Authority /O=HT srl | /CN=rcs-polluce | 277fdf33df7baca54ce8336982db865d9f38f514 |
| /CN=RCS Certification Authority /O=HT srl | /CN=RCS Certification Authority /O=HT srl | e8d5f17d142768abe2ed835d5a61d99602ab082b |
The file itself also matched a signature we had previously developed for RCS spyware.
https://citizenlab.org/2014/02/hacking-team-targeting-ethiopian-journalists/
No comments:
Post a Comment